Is it possible to have anonymous transactions on the public blockchain?

Many of today’s cryptocurrencies, including Bitcoin and Ethereum, are said to provide anonymity. But what exactly does it mean and, more importantly, is that true?
Privacy is not binary. It rather falls along a spectrum: from fully public to completely private. It’s hard to talk about hiding all data in a public, transparent blockchain, but can we hide just a part of the transaction, i.e. its author? That’s what I will discuss in this article. I will cover some of the possible techniques for achieving a reasonable level of anonymity using widely-known cryptocurrencies. If you are interested in creating a new blockchain check our blockchain development services.
Anonymity vs. privacy
To deeply understand the problem we’re about to face in this article, we need to define those two – in fact very different – concepts.
Anonymity “describes situations where the acting person’s name is unknown”. There is nothing about hiding the act itself.
Privacy – on the other hand – is defined as “the ability of an individual or group to seclude themselves, or information about themselves, and thereby express themselves selectively”
To make it clear, we can quite accurately state that anonymity is about hiding the “who”, while privacy is about hiding the “what”. In the context of blockchains, anonymity means the ability for parties to exchange data without disclosing any off-chain identity information or other transactions they have done. A simple example could be Bitcoin, which is partially anonymous (each address is nothing more than public key hash looking random), but not private at all (we know all transactions made from/to that address).
So, how is Bitcoin “partially anonymous”?
People like to think that Bitcoin makes their transactions anonymous. In fact, when making a BTC transaction, all its details, including source address, are permanently stored in the public ledger, which means anyone can see the balance and transaction history of any Bitcoin address. Such data remains anonymous as long as the author’s address cannot be linked with his physical identity. However, this can be difficult to achieve. The link happens, for example, when you sign up for an exchange that implements a KYC mechanism (most of them are enforced by law to do so). Or when you publish your address on your blog to get donations.
It’s true that you can generate a new address and use it to make an “anonymous” payment. Bitcoin’s original whitepaper recommends using a new address for each transaction. Doing so helps avoid transactions being linked to a common owner but also generates another set of problems. First, you have to top up the address you want to make a payment from. How? If you send funds from another one of your addresses, tracking this and eventually uncovering your identity will be trivially simple. It’s all about reading blockchain history (transaction graph analysis, taint analysis, tracking payments, web-spidering, and many other mechanisms) and looking over network traffic. Almost anyone with enough time and dedication can trace those pieces of information and connect them (see this video to better understand the process behind it). Moreover, since the Bitcoin network is an ordinary P2P, it exposes its users to a whole range of network-level attacks. Everybody who is between the user and the Bitcoin network (e.g. ISP) can reveal his IP address easily. As you know, an authority can demand access to this information. One of the US DEA representatives even admitted that they “actually want” criminals to keep using Bitcoin because it gives them “a lot of tools to be able to identify people”. The fact is, without using any of the techniques I’m about to present, Bitcoin is much less anonymous than the traditional banking system.
“The way information leaks during ordinary purchases makes it straightforward to link individuals with the Bitcoin transactions they make, even when purchasers use additional privacy protections.” ~ Steven Goldfeder, Princeton University.
Although many improvements can be expected in the future to improve privacy, currently Bitcoin doesn’t provide any better protocol level anonymous mechanisms and that’s how most of the well-known cryptocurrencies work. This system (often called “pseudonymity”) is like writing under a pseudonym. If a pseudonym is ever linked to the user behind it, the protection is gone. To be absolutely clear – that means deanonymization of all content the user ever posted under this pseudonym. As the blockchain is permanent, it’s obvious that something not traceable currently may become trivial to trace in the future. Learn more here.
Anonymity – what can we do better with Bitcoin?
Mixing services & decentralized mixing
There are a few things you can do to get the most out of Bitcoin. First of all, there are centralized mixing services that offer to effectively mix your tokens with the tokens of others. Mixers, also called tumblers, works by receiving and sending back the same amount of coins using independent Bitcoin addresses, thus breaking traceability and obscuring any links between participating users. And that’s basically all it does. It makes the trail hard to follow on the blockchain, but it’s nothing more than security through obscurity. Or you can call it virtual money laundering if you want.
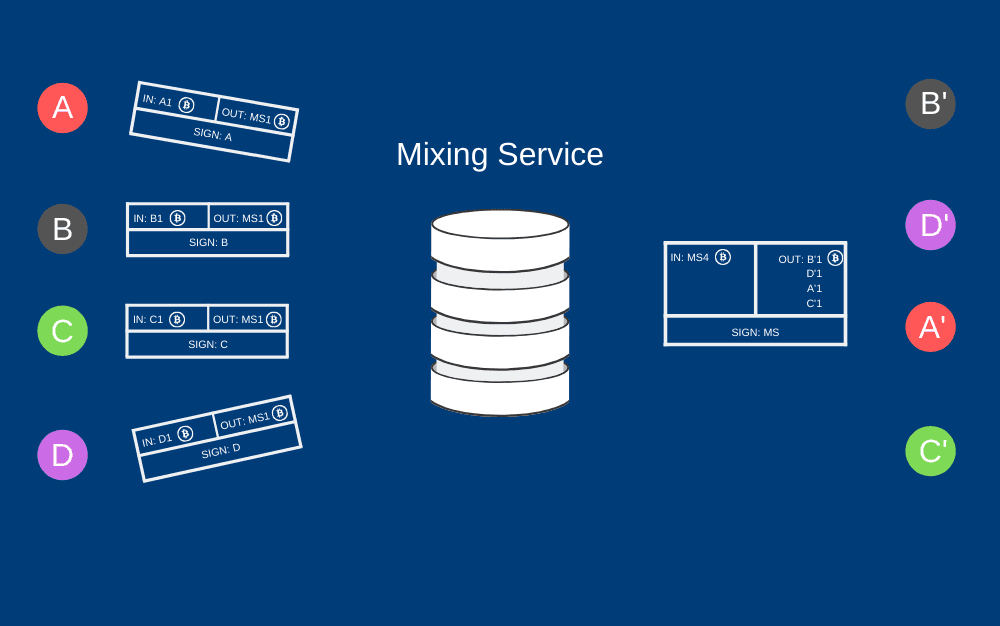
Simplified flow of mixing mechanism – each of A, B, C, D participants creates a transaction to the centralized Mixing Service. The service receives the funds and sends them back in a new transaction to addresses A’, B’, C’, D’ specified by the participants. From the blockchain observer point of view, a new address A’ appears with one received transaction from Mixing Service, but it’s hard to say who initiated and paid for it.
Also, there is a project called CoinJoin. It simply works by combining transaction inputs from multiple spenders into a single transaction. This may sound similar to mixers – the idea behind those is the same – make the connection between the input and the payee obfuscated. However, CoinJoin technique is much more sublime. It’s decentralized and requires no trust due to the use of multisignature between participants instead of some centralized party.
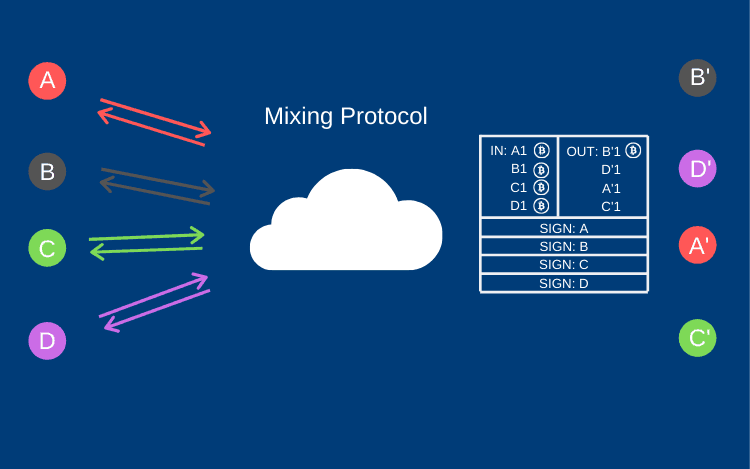
Simplified flow of decentralized mixing – group of A, B, C, D participants creates a multisig transaction to send funds to the new addresses A’, B’, C’, D’. This type of transaction requires each participant to sign it using their own private key. There is no risk of theft at any point. From the blockchain observer point of view, a new address A’ has received one transaction, but there is no way of knowing who of A, B, C, D created this specific output. Using only the blockchain analysis method, one can just find all the signers, but not the A -> A’ mapping.
Stealth addresses – “invisible” recipient
CoinJoin mechanism is used in some of the privacy-focused wallets (like Wasabi or Samourai) alongside with stealth addresses (also called ECDH address). These are one-time addresses generated by the sender for every transaction using the Elliptic-curve Diffie–Hellman (ECDH) protocol so that different payments made to the same receiver are unlinkable. It works as described below:
- The receiver has an ECDH key pair (b, B) (where b = private key, B = b * G = public key, G = EC base point)
- The sender generates one-time key pair (r, R) and transmits its public part R to the receiver (most often in a single transaction
- The receiver computes a shared secret: c = b * R = b * r * G
- The sender computes a shared secret: c = r * B = r * b * G
- The one-time address for this payment is: c * G + B
- The receiver can use the corresponding private key: c + b, to spend funds from this address.
To those of you who are new to EC cryptography: one could not simply compute private key r having R = r * G and knowing only R and G. The problem is known as discrete logarithm and it’s believed to be “hard”, meaning there is no known polynomial-time algorithm to solve it (in a classic cryptography the problem is: knowing a, b and prime p, find k such that b = a^k mod p). However, this implementation, known as Improved Stealth Address Protocol (ISAP) has a serious security flaw – it requires a transaction receiver to actively monitor newly generated address using his private spending key. Such a continuous usage of the key significantly increases the risk of it being recreated by an attacker. To eliminate this overuse, Dual-Key Stealth Address Protocol (DKSAP) was introduced. One key is used to spend the money and the other one is for generating and scanning a one-time address. This technique has been adopted by Monero, TokenPay and already mentioned Samourai Wallet, just to name a few.
Network-level anonymizers
Yet another idea is to use network-level anonymizers, like Tor (or I2P, Bitmessage, Freenet). That’s the thing others might recommend to you, but it produces yet another set of problems. Some of them are:
- Tor breaks in-built Bitcoin anti-DDos protection.
- Tor exit node can delay or drop transactions/blocks making double-spend possible.
- Tor introduces a chain of trust among its nodes, while Bitcoin is all about trustlessness.
- Tor network isn’t that secure. That should probably be discussed in a separate article, but it’s enough to mention obsolete algorithms used (RSA-1024, SHA1) and the relatively small number of active exit nodes.
Take a look at this great analysis of Bitcoin over Tor. All of this makes me hard to recommend this solution.
Buy it off a street corner
So, probably the best way to achieve anonymity in Bitcoin is: buy it off a street corner. Find anyone who can sell you BTC, meet him face-to-face, make a deal and pay him in good old cash. That’s simple.
There is a marketplace called localbitcoins.com that operates as an escrow service. It first holds the Bitcoin until the cash payment is done so both sides of the transaction are protected. The other places where you can find sellers nearby are facebook.com, meetup.com and similar. Of course, if you want to strengthen your privacy even further, you can use a VPN (or TOR) to search for a seller.
You may also consider Bitcoin ATMs, especially those that allow you to pay with cash. If they are actually available in your area, they can be really useful. After all, mix your fresh tokens using one of BTC launders. You are pretty hard to follow now.
Anonymity = pseudonymity + unlinkability
Now we’re one step away from understanding what true anonymity in the context of blockchain is. So, what is unlinkability? As a user interacts with the cryptocurrency network, different interactions should not be linkable to each other. That might mean the inability to:
- Link different addresses of the same user
- Link different transactions of the same user
- Link sender of a transaction to its recipient.
Are you thinking about mixers again? Their purpose is the same, but they guarantee nothing since they can’t vaporize data from the blockchain. Comparing to pseudonymity, the anonymity it’s like writing under no pseudonym so there is absolutely no way to your identity information to be leaked. That’s what some cryptocurrencies offer as one of the core features at the protocol level.
“Your keys, your bitcoin. Not your keys? Not your bitcoin.”~ Andreas M. Antonopoulos
Privacy coins and beyond
Several other concepts can be implemented to specifically address anonymity in the cryptocurrency industry. Dash uses PrivateSend (which is somehow similar to CoinJoin), and ZCash implements zero-knowledge-proof. There are Ring Signatures in Monero and MimbleWimble algorithms in Beam. All of this (and even more!) is covered below.
In the first part of this article, I’ve described the challenge of implementing anonymous transactions on the public blockchain. I proposed a bunch of solutions we can use to achieve this goal on most popular cryptocurrencies like Bitcoin or Ethereum, even though those coins do not really support anonymity. Luckily, besides that, there are cryptocurrencies focused mostly on privacy. They implement many of the already mentioned mechanisms on the protocol level, thus moving cryptocurrency anonymity to a different level.
Zero-knowledge proof
… or rather “zero-knowledge succinct non-interactive argument of knowledge” (zk-SNARK), as called by ZCash developers. zk-SNARK enables proving ownership of a given data without disclosing not only the data itself but any information about this data. In other words, it’s like Peggy wants to prove to Victor [13] that she knows a secret without telling him anything about the secret. That doesn’t sound very clear, so let’s explain the Ali Baba cave example from Wikipedia
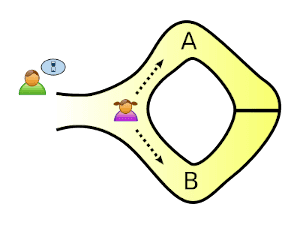
Let’s say we have a ring-shaped cave, with one entrance and a door blocking the way around. To unlock the door, Peggy must know the secret, and that’s what she wants to prove Victor.
She randomly takes either path A or B. The important part is that Victor knows nothing about the path she takes (that’s secret related information!).
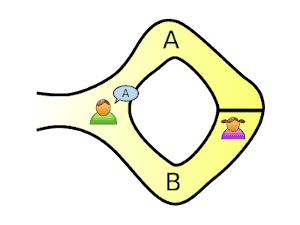
Victor chooses an exit path for Peggy. She opens the door if necessary, and returns along the desired path.
But if she doesn’t know the secret, she would only be able to return by the named path in 50% of the cases.
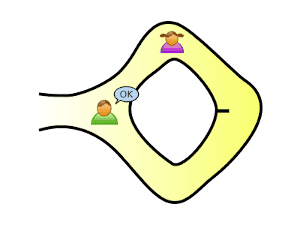
Let’s say Peggy appears at the exit Victor named. Repeat the process twice to be 75% sure she knows the secret. Repeat 20 times, and her chance of successfully appearing at the right exit becomes about one in a million.
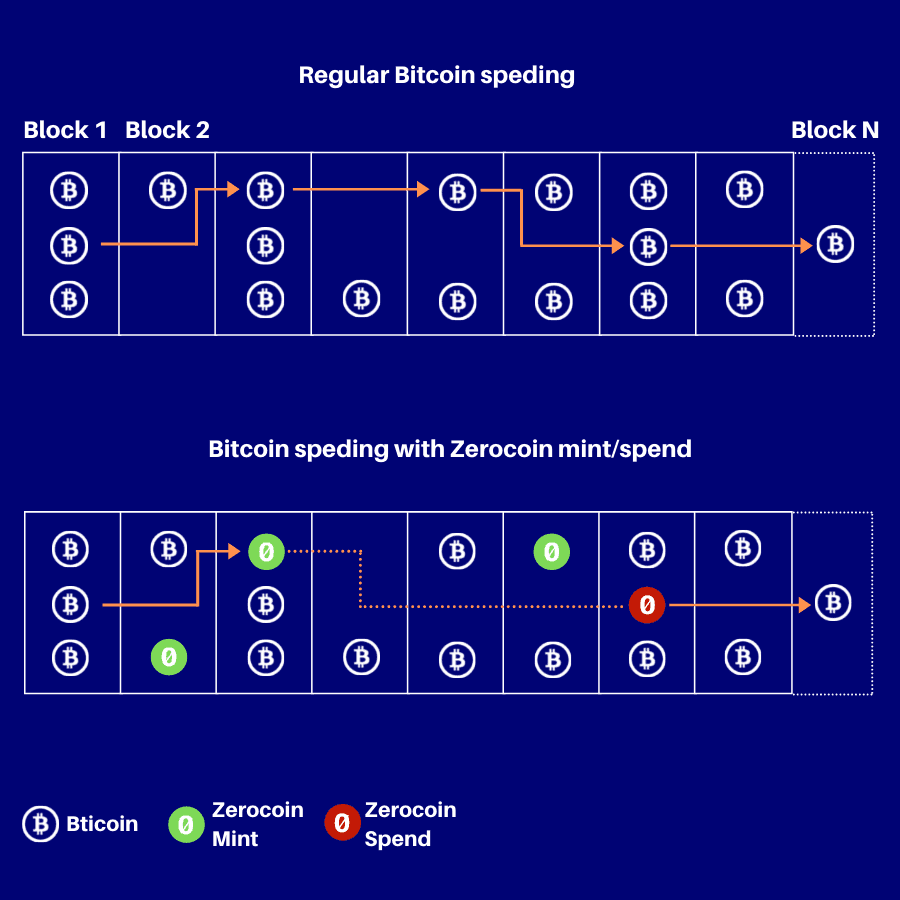
Zerocoin protocol
Zerocoin was proposed as an extension to the Bitcoin protocol that would provide true anonymity to transactions. Currently not compatible with Bitcoin, but available in stand-alone Zcoin and Anoncoin cryptocurrencies (alongside PIVX, SmartCash, Navcoin, and more. Some of them already opted-out from using Zerocoin protocol and migrated to other privacy solutions).
This protocol presupposes the existence of temporary, protocol-level Zerocoin tokens, existing on a base blockchain. The anonymity afforded here is obtained by separate Zerocoin mint and spend transactions. Minting is nothing more than burning some base currencies (e.g., Bitcoin) in exchange for Zerocoin tokens. The trick here is that you receive new, history-free tokens that are not linked in any way to coins you’ve burnt out. Single Zerocoin token is unique, can’t be duplicated or forged. To redeem it for the base currency, the owned of the token needs to prove the actual ownership. This is done by Zerocoin spend transaction and relies on zero-knowledge proof described above. After verification, the amount of the base currency equal to the Zerocoin denomination is transferred from the Zerocoin escrow pool. This might look similar to the mixing services, but is built-in into cryptocurrency’s protocol itself. However, Zerocoin requires significant computation time to work (mostly done by miners) and is the source of many security issues. Regardless, this protocol was one of the first solutions to the traceability problem in UTXO-based blockchains like Bitcoin.
Dash PrivateSend
Yet another method similar to coin-mixing and yet another with no 100% guarantee. Dash cryptocurrency utilizes the capability of masternodes, so the connection between the sender and receiver is untraceable. When the user wants to make an anonymous transaction, the PrivateSend function begins by splitting the inputs into discrete, non-unique relevant denominations (0.01 DASH, 0.1 DASH, 1 DASH, and 10 DASH). Then, a user’s wallet is initiating a request to randomly picked masternode to mix certain denominations of Dash coins. Within the mixing session, the masternode mixes up the inputs with two other masternodes, who has the same denominations. This process is repeated multiple times, so resulting coins are fully anonymized and obscured. Well, at least it’s said so. Some researches show there is a method of tracing PrivateSend transaction based on analyzing common origins between inputs on the same transaction. Using separate addresses for PrivateSend transactions solves this potential problem, though. Also, increasing the number of mixing rounds makes tracing exponentially more difficult. In the end, it all comes to the question of how secure you want (or need) to be.
Ring Signatures
In cryptography, Ring Signature is a type of digital signature that can be performed by any member of a group – each having separate keys. The goal is to sign the message as a particular group of people so that determining which of the group members’ keys was used to produce the signature is computationally infeasible. The cryptocurrency Monero was the first which adopted this method for anonymizing transactions. Their RingCT (Ring Confidential Transactions) algorithm hides the transaction amount and the identity of the payer and recipient, meaning that no one (except the sender and the receiver) can track any transaction details. What’s also nice about this approach is that it doesn’t rely on a centralized entity and – unlike things like CoinJoin or other mixers – you don’t need to collaborate with anyone to perform such anonymous transactions.
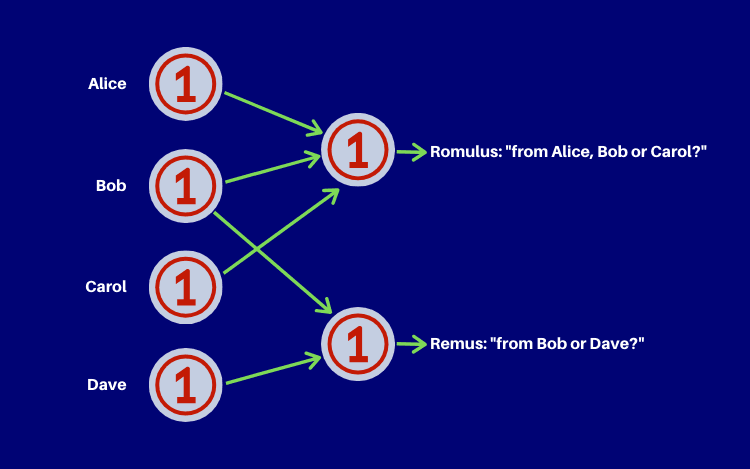
Blind Signatures
A blind signature is a kind of digital signature in which the message is disguised before it is signed so that even the signer itself will not learn the message content. That mechanism allows the signer and message author to be different parties. To verify the signature, one need to unblind the message first, but such operation tells nothing about the message author. Blind Signature schemes can be implemented over a number of common public key signing algorithms, such as RSA, DSA, or even on the elliptic curve. They are widely used in Smart Contracts, for example, when implementing an anonymous e-voting system.
MimbleWimble
MimbleWimble is a blockchain protocol focused on privacy, fungibility, and scalability. Although, the word comes from the magic world of Harry Potter, also known as the Tongue-Tying Spell is a curse that prevents your opponent from accurately casting their next spell.
It proposes a set of changes in the UTXO model and PoW consensus algorithm to be able to:
- Hide sender and receiver addresses.
- Hide amount transferred.
- Join two transactions, in which the second one is spending the first one in a way that every intermediate information vanishes.
To achieve the first goal, CoinJoin (already described in the first part of this article) is used. The second trick is Confidential Transaction (CT) – a cryptographic protocol that results in the amount value of a transaction being encrypted so that every network member is still able to verify that amount, but without revealing the exact value. This relies on the mentioned above Blind Signatures and Homomorphic encryption. The third technology here is well known Merkle Tree. MimbleWImble uses it to encrypt transactions at the node level and then join them together under a number of conditions. This also allows us to significantly reduce blockchain size since many intermediate pieces of information are not really needed to verify the resulting transaction and might be securely removed from the blockchain.
MimbleWimble is mostly known for being implemented in Beam and Grin cryptocurrencies.
Summary
In this article, I have covered techniques for achieving a reasonable level of anonymity using widely-known cryptocurrencies. If you find this topic interesting or want to explore it further, you are welcome to contact us. If you are interested in creating a new blockchain or cryptocurrency exchange check our blockchain development services.