Biometric authentication in Android fintech apps
Biometric authentication in fintech apps is like having a personal bouncer for your digital wallet.
It uses unique biological traits – your fingerprint, face, or iris – to guard your financial data. This isn’t just a fancy lock; it’s becoming the gold standard for securing mobile finance.
Why the buzz?
In this article, we’ll decode biometric authentication for Android fintech apps. We’ll explore its types, how to implement it, best practices, and peek into its future.
Whether you’re coding the next big finance app or just curious about what’s guarding your digital assets, stick around. We’re about to press our thumbs to the screen and unlock the secrets of biometric security in Android fintech apps.
What are biometrics?
Biometrics blend what you are with what you have. Your fingerprint plus your phone creates a fortress around sensitive info.
It’s faster than typing passwords and tougher to crack than your pet’s name followed by ‘123’.
For fintech, where every second and every bit of security counts, biometrics offer a compelling mix of speed and safety. It’s like having the convenience of a house key with the security of a bank vault.
How does biometric authentication stack up against traditional login methods?
Biometric authentication vs. traditional login authentication methods. Comparison
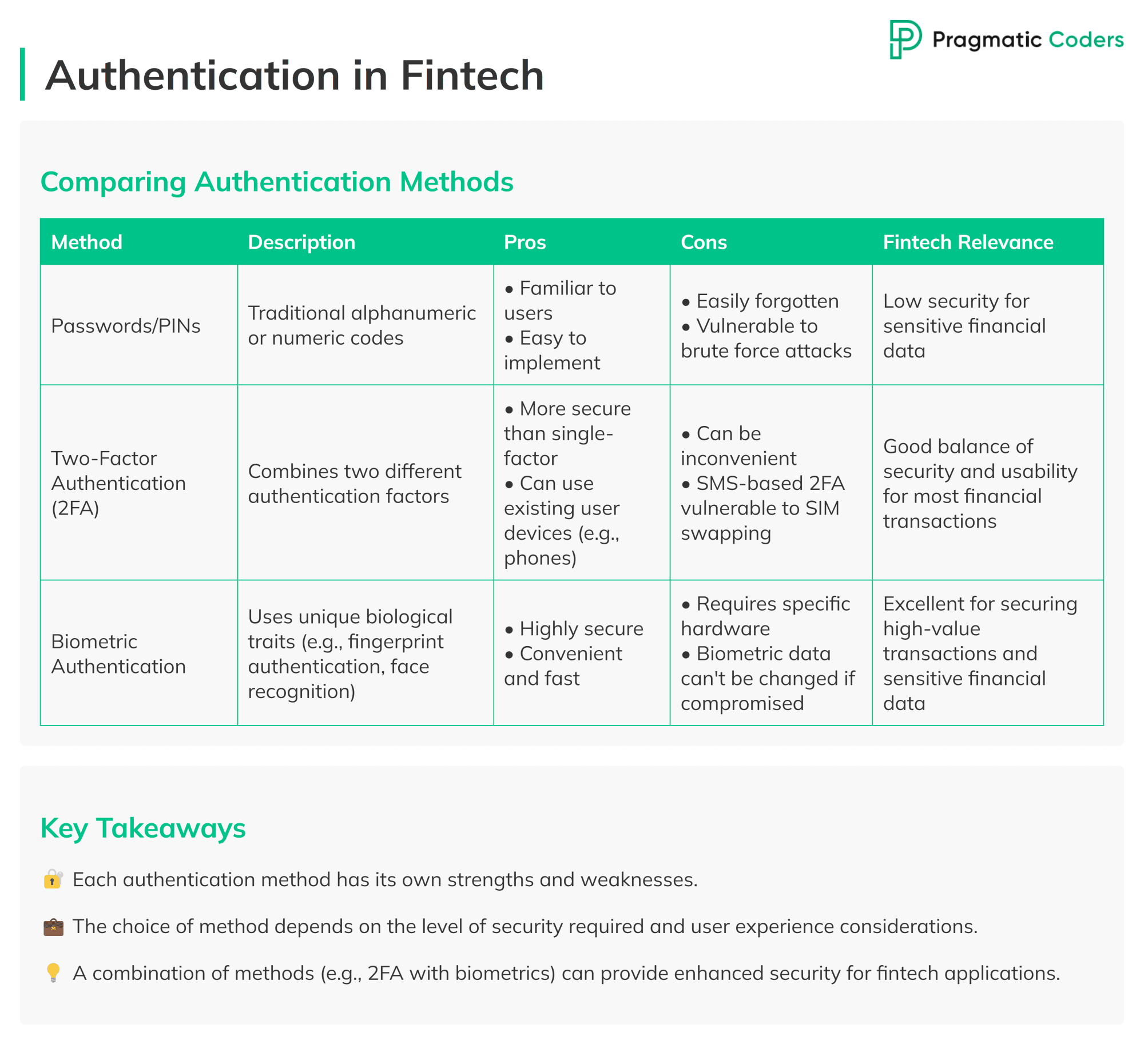
Passwords and PINs
Passwords and PINs represent the traditional approach to digital security. They are widely recognized by users and straightforward for organizations to implement.
The minus of this method? Significant limitations.
Users frequently struggle to remember them, leading to frustration and potential security risks.
More critically, these methods are vulnerable to brute force attacks, where hackers systematically attempt various combinations to gain unauthorized access. Due to these weaknesses, passwords and PINs are not ideal for safeguarding sensitive financial data.
Two-factor authentication (2FA)
Two-factor authentication enhances security by requiring two distinct forms of identification.
This often involves entering a password followed by a unique code sent to a personal device. 2FA significantly improves security compared to single-factor methods. It typically utilizes devices users already possess, such as smartphones, which adds convenience.
Yet, it’s not without drawbacks. The additional step can sometimes be cumbersome for users, and SMS-based 2FA is potentially vulnerable to SIM swapping attacks.
Despite these concerns, 2FA offers a balanced approach to security and usability for most financial transactions.
Biometric authentication
Biometric authentication utilizes unique physical characteristics like fingerprints or facial features to verify identity.
This method provides a high level of security due to the difficulty of replicating these traits. It offers both efficiency and convenience, as it allows users to authenticate quickly through interaction with a sensor or camera.
However, biometric systems require specialized hardware, which can increase implementation costs. Additionally, there are privacy considerations to address. Unlike passwords, biometric data cannot be altered if compromised.
Nonetheless, biometric authentication remains highly effective for protecting high-value transactions and sensitive financial information.
Key takeaways for fintech
- Passwords alone are insufficient for protecting sensitive financial information.
- 2FA provides a good security boost but may not be enough for high-value transactions.
- Biometric authentication offers the best combination of security and user experience for most fintech applications.
- A layered approach, combining multiple methods, often provides the best security for fintech apps.
Types of Android biometric authentication
Android devices offer a variety of biometric authentication methods, each like a unique key to your digital vault.
Let’s explore the main types:
- Fingerprint recognition: The most common method. It’s your fingertip’s unique pattern acting as a password.
- Facial recognition: Uses your face as the key. It’s like having a doorman who knows you by sight.
- Iris scanning: Less common but highly secure. It’s akin to a retinal scanner from a sci-fi movie.
In fintech apps, the choice often depends on device capabilities and security needs. Here’s a unified approach to implement any of these methods:
| private fun showBiometricPrompt() { val promptInfo = BiometricPrompt.PromptInfo.Builder() .setTitle(“Secure Financial Access”) .setSubtitle(“Verify your identity”) .setNegativeButtonText(“Cancel”) .build()
// require(context is FragmentActivity) val biometricPrompt = BiometricPrompt(context, executor, object : BiometricPrompt.AuthenticationCallback() { override fun onAuthenticationSucceeded( result: BiometricPrompt.AuthenticationResult ) { Log.d(“FINTECH_APP”, “Access granted!”) proceedWithFinancialOperation() } // Handle other callbacks… })
biometricPrompt.authenticate(promptInfo) } |
This approach allows your fintech app to adapt to available biometric capabilities, providing a seamless and secure authentication experience across different devices.
Biometric authentication classes
Android categorises biometric authentication into three classes, each offering different security levels crucial for fintech applications:
The Spoof Acceptance Rate (SAR) is a critical metric used to evaluate the security of biometric authentication systems in Android devices. It measures the likelihood that a biometric system will incorrectly accept a spoofed sample, which is a fake representation of a user’s biometric data (e.g., a fingerprint or voice recording).
- Class 3 (Strong):
- Highest security, ideal for high-value transactions
- Spoof Accept Rate (SAR) < 7%
- Use for: Large fund transfers, accessing critical financial data
- Class 2 (Weak):
- Medium security, suitable for most financial operations
- SAR < 20%
- Use for: Regular transactions, account management
- Class 1 (Convenience):
- Basic level, not recommended for sensitive financial operations
- No specific security requirements
- Use for: Checking account balances, low-risk activities
When implementing biometric authentication in your fintech app, specify the required security level:
| val promptInfo = BiometricPrompt.PromptInfo.Builder() .setTitle(“Authenticate for Transaction”) .setSubtitle(“Biometric authentication required”) .setAllowedAuthenticators(BiometricManager.Authenticators.BIOMETRIC_STRONG) .build() |
By using BIOMETRIC_STRONG, you ensure only Class 3 biometrics are used, providing maximum security for sensitive financial operations.
Remember: The choice of biometric class should align with the sensitivity of the data or operation being protected.
For fintech apps, prioritising stronger authentication (Class 3) is often the prudent choice, especially for critical financial transactions or accessing highly sensitive data.
Implementing biometric authentication in Android
Repository: https://github.com/pragmaticcoders/android-biometric-auth
Now that we understand the types and classes of biometric authentication, let’s roll up our sleeves and implement it in an Android fintech app. Think of this as assembling your high-tech security system, piece by piece.
Step 1: Set up dependencies
Add the androidx biometric library to your app’s build.gradle file:
| dependencies { implementation “androidx.biometric:biometric:1.1.0” } |
Step 2: Create the biometrics class
Create a Biometrics class to encapsulate all biometric-related functionality:
| class Biometrics { // We’ll add the contents in the following steps } |
Step 3: Define authentication results
Inside the Biometrics class, define a sealed interface for authentication results:
| sealed interface AuthenticationResult { object Success : AuthenticationResult object Failure : AuthenticationResult object AuthenticationNotSet : AuthenticationResult object HardwareUnavailable : AuthenticationResult object FeatureUnavailable : AuthenticationResult data class Error(val errorMessage: String) : AuthenticationResult } |
Step 4: Set up result emission
Use MutableSharedFlow to emit authentication results:
| private val mutableSharedFlow = MutableSharedFlow<AuthenticationResult>() val sharedFlow = mutableSharedFlow.asSharedFlow() |
Step 5: Implement the Authentication Function
Create the authenticate function:
| fun authenticate(context: Context) { require(context is FragmentActivity) { “Context must be an instance of FragmentActivity” }
val manager = BiometricManager.from(context)
val authenticators = when { android.os.Build.VERSION.SDK_INT >= android.os.Build.VERSION_CODES.R -> { BIOMETRIC_STRONG or DEVICE_CREDENTIAL } else -> { BIOMETRIC_STRONG } }
// … (continue with the rest of the function) } |
Step 6: Set up the biometric prompt
Inside the authenticate function, create and configure the BiometricPrompt:
| val promptInfoBuilder = BiometricPrompt.PromptInfo.Builder() .setTitle(“Secure Financial Transaction”) .setSubtitle(“Authenticate to proceed with your transaction”) .setAllowedAuthenticators(authenticators)
if (android.os.Build.VERSION.SDK_INT < android.os.Build.VERSION_CODES.R) { promptInfoBuilder.setNegativeButtonText(“Cancel”) } |
Step 7: Check biometric availability
Still in the authenticate function, check if biometric authentication is available:
| val canAuthenticate = when (manager.canAuthenticate(authenticators)) { BiometricManager.BIOMETRIC_SUCCESS -> true BiometricManager.BIOMETRIC_ERROR_HW_UNAVAILABLE -> { mutableSharedFlow.tryEmit(AuthenticationResult.HardwareUnavailable) false } // … (handle other cases) } |
Step 8: Implement authentication callback
If biometric authentication is available, create and use the BiometricPrompt:
| if (canAuthenticate) { val prompt = BiometricPrompt( context, object : BiometricPrompt.AuthenticationCallback() { override fun onAuthenticationSucceeded(result: BiometricPrompt.AuthenticationResult) { super.onAuthenticationSucceeded(result) mutableSharedFlow.tryEmit(AuthenticationResult.Success) }
override fun onAuthenticationFailed() { super.onAuthenticationFailed() mutableSharedFlow.tryEmit(AuthenticationResult.Failure) }
override fun onAuthenticationError(errorCode: Int, errString: CharSequence) { super.onAuthenticationError(errorCode, errString) mutableSharedFlow.tryEmit(AuthenticationResult.Error(errString.toString())) } } )
prompt.authenticate(promptInfoBuilder.build()) } |
Step 9: Use the “biometrics” class in your activity
In your activity or fragment, create an instance of the Biometrics class and use it:
| class FinancialTransactionActivity : FragmentActivity() { private val biometrics = Biometrics()
override fun onCreate(savedInstanceState: Bundle?) { super.onCreate(savedInstanceState) setContentView(R.layout.activity_financial_transaction)
findViewById<Button>(R.id.buttonMakeTransaction).setOnClickListener { biometrics.authenticate(this) }
// Observe authentication results lifecycleScope.launch { biometrics.sharedFlow.collect { result -> when (result) { is Biometrics.AuthenticationResult.Success -> { // Proceed with transaction } is Biometrics.AuthenticationResult.Failure -> { // Handle failure } // Handle other cases… } } } } } |
By following these steps, you’ve implemented a robust biometric authentication system in your fintech app. It’s like installing a high-tech security system in a bank – it provides a strong layer of protection for sensitive financial operations.
Remember, in a fintech context, it’s crucial to combine this with other security measures and follow best practices, which we’ll cover in the next section.
Cryptographic operations with biometric authentication
In fintech, combining biometrics with cryptography is crucial. It’s like adding a DNA scanner to your vault, providing an extra security layer for sensitive financial data.
CryptoObject: Your biometric briefcase
Android’s CryptoObject acts as a secure briefcase, unlocked only by the right biometric key. Here’s how to use it:
| private lateinit var biometricPrompt: BiometricPrompt private lateinit var promptInfo: BiometricPrompt.PromptInfo
private fun setupBiometricCrypto() { val cipher = getCipher() val cryptoObject = BiometricPrompt.CryptoObject(cipher)
biometricPrompt = BiometricPrompt(this, executor, object : BiometricPrompt.AuthenticationCallback() { override fun onAuthenticationSucceeded(result: BiometricPrompt.AuthenticationResult) { val authenticatedCipher = result.cryptoObject?.cipher encryptSensitiveData(authenticatedCipher) } })
promptInfo = BiometricPrompt.PromptInfo.Builder() .setTitle(“Authenticate for Secure Transaction”) .setSubtitle(“Use your biometric to encrypt data”) .setNegativeButtonText(“Cancel”) .build()
// Initiate biometric authentication with CryptoObject biometricPrompt.authenticate(promptInfo, cryptoObject) }
private fun encryptSensitiveData(cipher: Cipher?) { cipher?.let { val encryptedData = it.doFinal(“Sensitive financial data”.toByteArray()) // Store or transmit encryptedData securely } } |
This approach ensures that even if encrypted data is intercepted, it remains unreadable without biometric authentication. It’s particularly crucial for high-value transactions or extremely sensitive financial information in your fintech app.
By integrating cryptographic operations with biometrics, you’re not just locking the door – you’re securing the entire vault of user financial data.
Privacy and security concerns
In fintech, protecting user data is paramount. Biometric authentication adds a layer of security, but also introduces new considerations:
Data storage: Android’s biometric APIs are designed with privacy in mind. Biometric data never leaves the device, staying in secure hardware-backed storage. Your app only receives a yes/no authentication result, never the actual biometric data.
Regulatory compliance: Fintech apps must navigate regulations like GDPR and PSD2:
- GDPR: Obtain explicit consent for biometric use and offer opt-out options.
- PSD2: Implement strong customer authentication, potentially combining biometrics with another factor for high-value transactions.
User trust: Transparency is key. Clearly communicate how biometric data is used and protected. Always provide alternative authentication methods for users who can’t or prefer not to use biometrics.
Security best practices
- Conduct regular security audits of your biometric implementation.
- Stay current with Android security patches and biometric API updates.
- Implement secure fallback mechanisms for authentication failures.
By addressing these concerns, fintech apps can leverage the security benefits of biometrics while maintaining user trust and regulatory compliance. Remember, in fintech, security isn’t just about technology—it’s about safeguarding people’s financial lives.
Future trends in biometric authentication
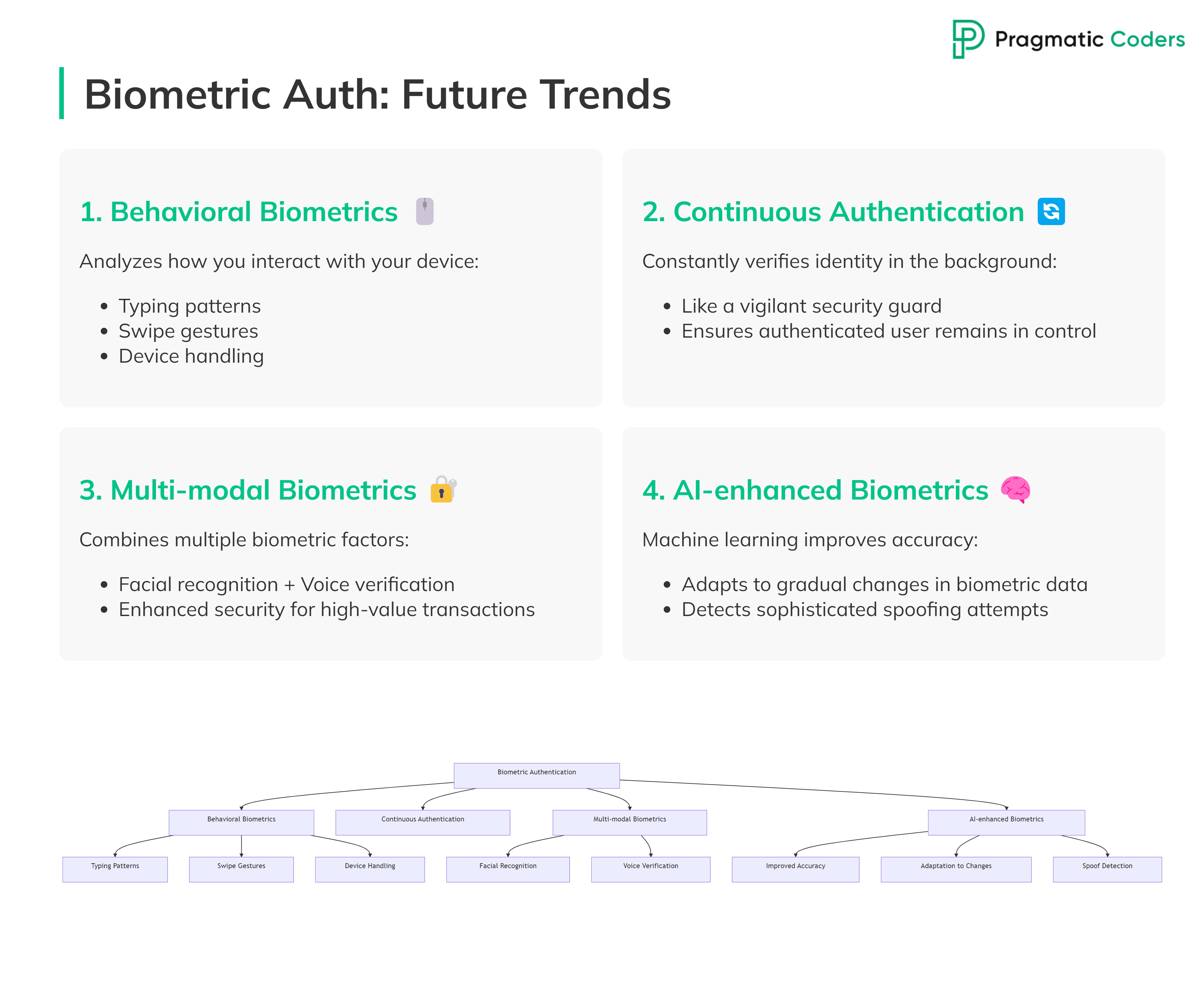
The fintech security landscape is evolving rapidly. Here are key trends shaping the future of biometric authentication:
- Behavioral biometrics: Beyond physical traits, future systems may analyze how you interact with your device. This includes typing patterns, swipe gestures, and even how you hold your phone. It’s like recognizing someone by their unique mannerisms, not just their face.
- Continuous authentication: Instead of one-time checks, systems might constantly verify your identity in the background. Imagine a security guard who doesn’t just check your ID at the door but keeps an eye on you throughout your visit. This ensures the authenticated user remains in control throughout the session.
- Multi-modal biometrics: Combining multiple biometric factors enhances security. For instance, an app might use both facial recognition and voice verification for high-value transactions. It’s like using both a retinal scan and a fingerprint to access a vault.
- AI-enhanced biometrics: Machine learning algorithms could improve accuracy and adapt to gradual changes in biometric data. This might include:
- Improving recognition accuracy over time
- Adapting to slight changes in user biometrics (e.g., aging effects)
- Detecting sophisticated spoofing attempts
These advancements aim to create a seamless, secure experience that knows you almost as well as you know yourself, while staying one step ahead of potential threats in the fast-paced world of finance.
See also:
Conclusion
Biometric authentication is transforming security in Android fintech apps. It offers a powerful blend of convenience and protection, surpassing traditional methods.
Key takeaways:
- Android supports various biometric types, each with unique strengths.
- Biometric classes (1, 2, 3) provide a framework for implementing appropriate security levels.
- The BiometricPrompt API streamlines implementation for developers.
- Best practices include combining biometrics with other security measures and prioritizing user privacy.
- Future trends point towards more sophisticated, AI-enhanced biometric systems.
For fintech developers, embracing biometric authentication is crucial for building trust and staying competitive. It’s not just about protecting data—it’s about safeguarding people’s financial lives.
As biometrics and finance continue to merge, we’re entering a new era of digital security. The future of fintech is literally at our fingertips, offering simpler yet more secure access to our finances than ever before.
If you’re looking to integrate biometric authentication into your fintech app, our team of experts can help you develop a secure and user-friendly solution. Contact us >>







