Open Banking API Security: Best Practices for Fintechs

Open Banking is shaking up the financial world, offering fresh ways to innovate. APIs play a crucial role in this transformation by enabling secure data sharing between financial institutions and third-party providers. But with new opportunities come new risks, and that’s where security comes into play… Did you know security breaches cost companies an average of $4 million?
For fintechs, securing APIs isn’t just about following rules—it’s about protecting your reputation and keeping customer trust. In this article, we’ll walk you through the steps to secure your Open Banking APIs. This way, you stay ahead of threats and keep your data safe.
But first, a quick definition:
An API, or Application Programming Interface, lets different software applications talk to each other. In Open Banking ecosystem, APIs enable secure data sharing between banks and fintechs. This means fintechs can access customer account info, initiate payments, and create innovative services. APIs are the backbone of Open Banking, making seamless and secure interactions possible.
Key Points
|
Why API Security is Vital in Open Banking
For fintechs, securing APIs isn’t just about ticking boxes—it’s about protecting your business and keeping your customers’ trust intact. A breach can do more than hurt your bottom line; it can shatter your reputation and erode the trust customers place in you to keep their most sensitive information safe, from bank details to transaction histories. In fact, enhancing cybersecurity is one of the top trends in banking technology today. As security expectations rise, making sure your APIs are secure is crucial. Once trust is broken, it’s tough to win back, so staying ahead on security is key to long-term success.
Beyond trust, there are regulations to consider. Laws like the Payment Services Directive 2 (PSD2) in Europe and the California Consumer Privacy Act (CCPA) in the USA require strong security measures for APIs. Failure to comply can lead to heavy fines and legal trouble, so securing your APIs is essential.
A Brief Look at Regulatory Requirements
To keep things above board, fintechs need to navigate a maze of regulations aimed at protecting consumer data. In Europe, the PSD2 mentioned above is a major player. It demands strong customer authentication (SCA) and secure communication through APIs, ensuring that only the right people can access financial data.
In the USA, the CCPA focuses on data privacy. It gives consumers more control over their personal information, which means your APIs need to be rock solid. Falling short on these requirements can cost you big time, both in fines and in lost business.
Navigating these regulations is no small task. This is where expert fintech software development comes in. With the right partner, you can integrate and secure APIs in compliance with PSD2, CCPA, and other regulations. This ensures your business stays ahead of security threats and meets the demands of a fast-moving industry. Investing in professional development services can make the difference between merely complying and thriving in the fintech space.
Key API Vulnerabilities in Open Banking
APIs are the backbone of Open Banking, but they’re also prime targets for cyberattacks. Here are some common vulnerabilities:
- Weak Authentication: Without strong authentication, attackers can easily gain unauthorized access. Using outdated or weak methods makes it easy for hackers to impersonate users and steal sensitive information.
- Data Exposure: APIs handle critical data, like account details and transaction histories. If this data isn’t encrypted, it’s at risk of being intercepted by attackers. Encryption is a must to keep data secure during transmission.
- No Rate Limiting: Without rate limiting, APIs are susceptible to brute force attacks. Hackers can flood your API with requests, trying different combinations until they find a way in. Rate limiting controls the number of requests, helping to prevent these attacks.
- Poor Input Validation: If your API doesn’t properly validate inputs, it’s susceptible to injection attacks. This is where attackers send malicious data through the API, potentially gaining access to your systems or corrupting your data.
- Detailed Error Messages: Providing too much information in error messages can be dangerous. Attackers can use these details to learn more about your system’s vulnerabilities and craft more effective attacks.
Real-World Examples of API Breaches
API breaches aren’t just theoretical—they’ve happened, with serious consequences:
- Capital One (2019): A misconfigured API led to a breach that exposed the personal information of over 100 million customers. The attacker exploited a weakness in the API’s firewall to gain access to customer data. This caused a major financial and reputational hit for Capital One.
Cosmos Bank (India, 2018): Attackers used an API vulnerability to authorize fraudulent transfers. Result: nearly $13.5 million stolen. This breach underscores how a single API weakness can lead to massive financial losses.
These incidents show how crucial it is to secure your APIs. A breach doesn’t just cost money—it can destroy trust and lead to regulatory penalties.
The Impact on Trust and Compliance
When a security breach occurs, the ripple effects can be severe:
- Loss of Customer Trust: Customers expect fintechs to protect their data. A breach can shatter this trust, driving customers to competitors who offer stronger security. Once lost, trust is incredibly difficult to rebuild.
- Regulatory Scrutiny: Breaches often bring regulatory consequences. As already mentioned, regulations mandate strict security measures for APIs. Non-compliance can result in hefty fines and legal challenges, adding to the financial damage of a breach. Just how substantial are these fines? Under the GDPR, fines can reach up to €20 million or 4% of the company’s global annual revenue, whichever is higher.
Best Practices for Securing Open Banking APIs
Securing your banking APIs is crucial for protecting sensitive data, maintaining customer trust, and staying compliant. To help you implement robust security measures, here’s a comprehensive API development guide with best practices every API developer should follow.
Implement Strong Authentication and Authorization
Authentication and authorization are your first lines of defense. Without them, anyone could access sensitive data.
- Use OAuth 2.0: OAuth 2.0 is the go-to standard for secure authorization. It allows third-party apps to access data without exposing user credentials. By using OAuth 2.0, you can control who accesses your APIs, keeping unauthorized users out.
- Manage API Keys Carefully: API keys control access to your APIs, so it’s essential to manage them securely. Don’t hard-code keys in your app. Store them securely and rotate them regularly. Monitor their usage to catch any suspicious activity.
Data Encryption and Tokenization
Protecting the data your APIs handle is non-negotiable. Here’s how to keep it safe:
- Encrypt Data in Transit and at Rest: Encryption is your shield. It ensures that even if data is intercepted, it’s unreadable without the proper decryption key. Use strong encryption methods like TLS for data in transit, and make sure data at rest is also encrypted. This keeps your data safe from prying eyes.
- Tokenize Sensitive Information: Tokenization replaces sensitive data with tokens that have no value to hackers. Even if someone gains access, they won’t be able to use the data. Tokenization is especially useful for protecting things like payment details or account numbers.
Regular Security Audits and Penetration Testing
Testing your APIs regularly is key to staying secure.
- Conduct Regular Security Audits: Security audits help you spot weaknesses before hackers do. Regularly check your security policies, access controls, and API configurations. Make this a habit, not a one-off task.
- Do Penetration Testing: Penetration testing simulates an attack on your APIs to find vulnerabilities. It’s better to find and fix these issues yourself than let a hacker exploit them. Regular testing helps you stay ahead of the game.
- Integrate Security into CI/CD: Security shouldn’t be an afterthought—it should be part of your development process. Build automated security testing into your Continuous Integration/Continuous Deployment (CI/CD) pipeline. This way, you catch issues early and only deploy secure code.
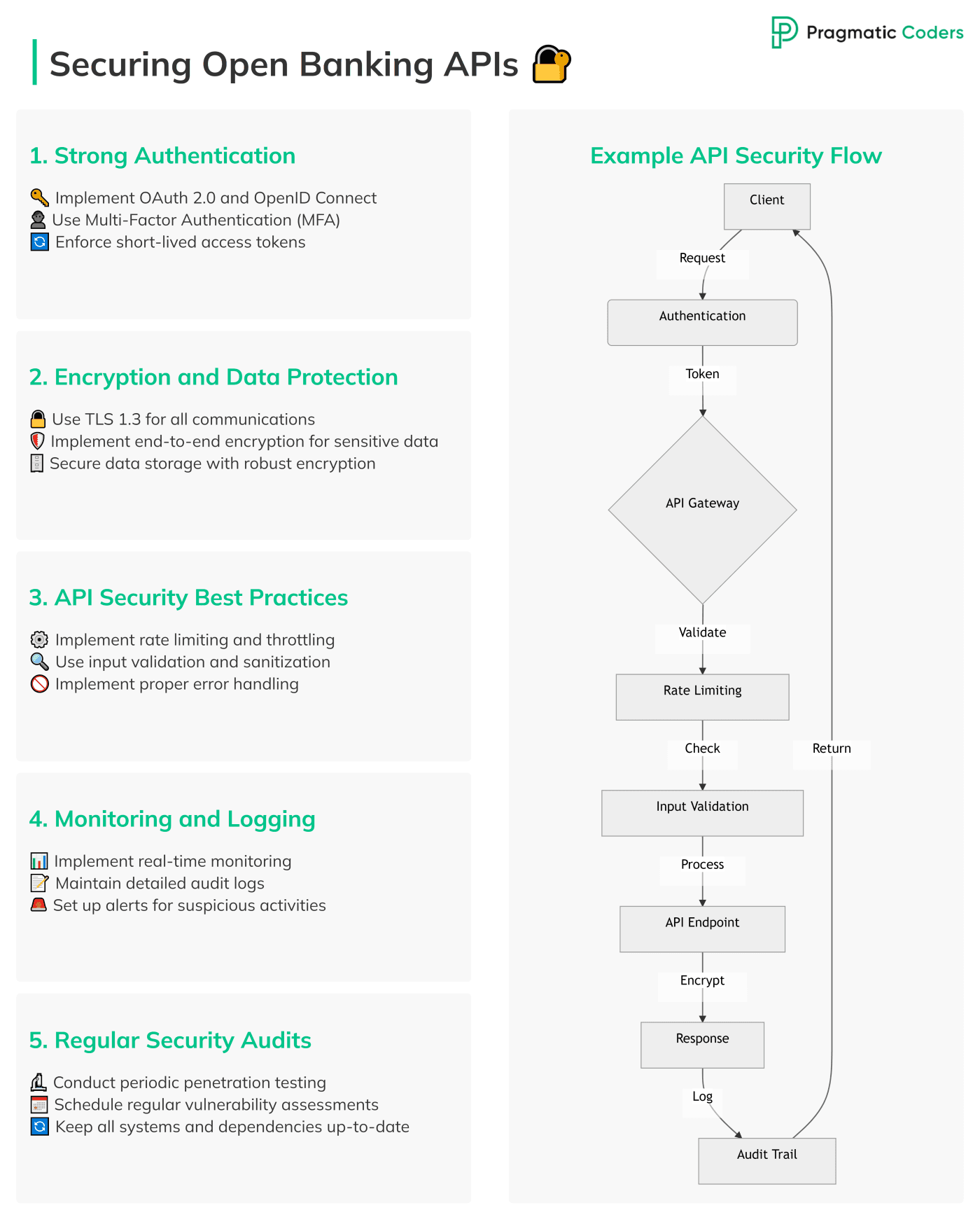
Advanced Security Measures for Open Banking APIs
Basic security practices are vital, but as threats become more complex. Thus, you need to step up your game. Here are some advanced security measures to help protect your Open Banking APIs from more sophisticated attacks.
Rate Limiting and Throttling
Your APIs can be bombarded with too many requests in a short time, leading to Denial of Service (DoS) attacks. This can disrupt services for legitimate users.
Preventing DoS Attacks: Rate limiting and throttling are essential to managing API traffic and preventing attacks. By controlling how many requests a user can make within a certain timeframe, you can stop your API from being overwhelmed. For instance, you could set a limit of 100 requests per minute per user. This helps prevent attackers from overloading your system and keeps your API available for genuine users.
Implementing an API Gateway
As your API setup expands, managing and securing multiple APIs can get tricky. This is where an API gateway becomes essential.
Centralizing Security Controls: An API gateway acts as the single entry point for all your APIs. It handles important tasks like routing requests, applying rate limits, and enforcing security policies. Centralizing these controls ensures that security is consistent across all your APIs. It also makes it easier to monitor and respond to potential threats.
Advanced Threat Detection and Prevention
Threats are always evolving, so your security measures need to keep up.
Using AI and Machine Learning: Modern threat detection tools use AI and machine learning to analyze traffic patterns in real-time. They can spot unusual activities, like spikes in requests or attempts to access unauthorized data, that might indicate an attack. By catching these signs early, you can prevent a breach before it happens.
Deploying API Firewalls: An API firewall adds another layer of protection by filtering incoming and outgoing traffic. It blocks malicious traffic—like SQL injections or cross-site scripting—before it can reach your API. Such firewall acts as an outer perimeter in defending against a wide range of threats.
Compliance with Regulatory Standards
Securing your Open Banking APIs isn’t just about keeping data safe—it’s also about meeting regulatory requirements. Staying compliant is crucial to avoid fines, legal issues, and losing customer trust. Here’s how to make sure your API security practices align with key regulations, maintain proper documentation, and handle customer data responsibly.
Aligning API Security with Regulatory Requirements
Regulations like GDPR and PCI DSS set strict standards for how data should be protected. For Open Banking APIs, following these regulations is a must.
- GDPR: The GDPR is all about protecting personal data. For APIs, this means ensuring that any personal information exchanged is encrypted. Data access must be tightly controlled. Users should have control over their data. Strong authentication, encryption, and access controls are crucial to staying compliant with GDPR.
- PCI DSS: If your APIs handle payment information, PCI DSS compliance is a must. This standard requires payment data to be encrypted. Your security measures should be tested regularly. Access to payment data must be strictly controlled. Meeting these standards helps you avoid fines and keeps customer payment details secure.
Keeping your API security practices aligned with these regulations requires regular reviews. Make sure your security measures meet the latest standards. Regulations can change, so staying up to date is key.
Documentation and Reporting for Regulatory Compliance
Good documentation is essential for proving compliance. Regulators often require detailed records of how you secure your APIs and protect customer data.
- Keep Detailed Records: Document everything—your encryption methods, access controls, and authentication processes. Record any changes you make to your security policies. This documentation helps you stay compliant and gives you a clear record if you’re ever audited.
- Regular Reporting: Regularly report your compliance status to the relevant authorities. This could include security audit results, penetration testing reports, and any data breaches. Being transparent about your security efforts shows that you’re serious about compliance. And it helps you avoid penalties.
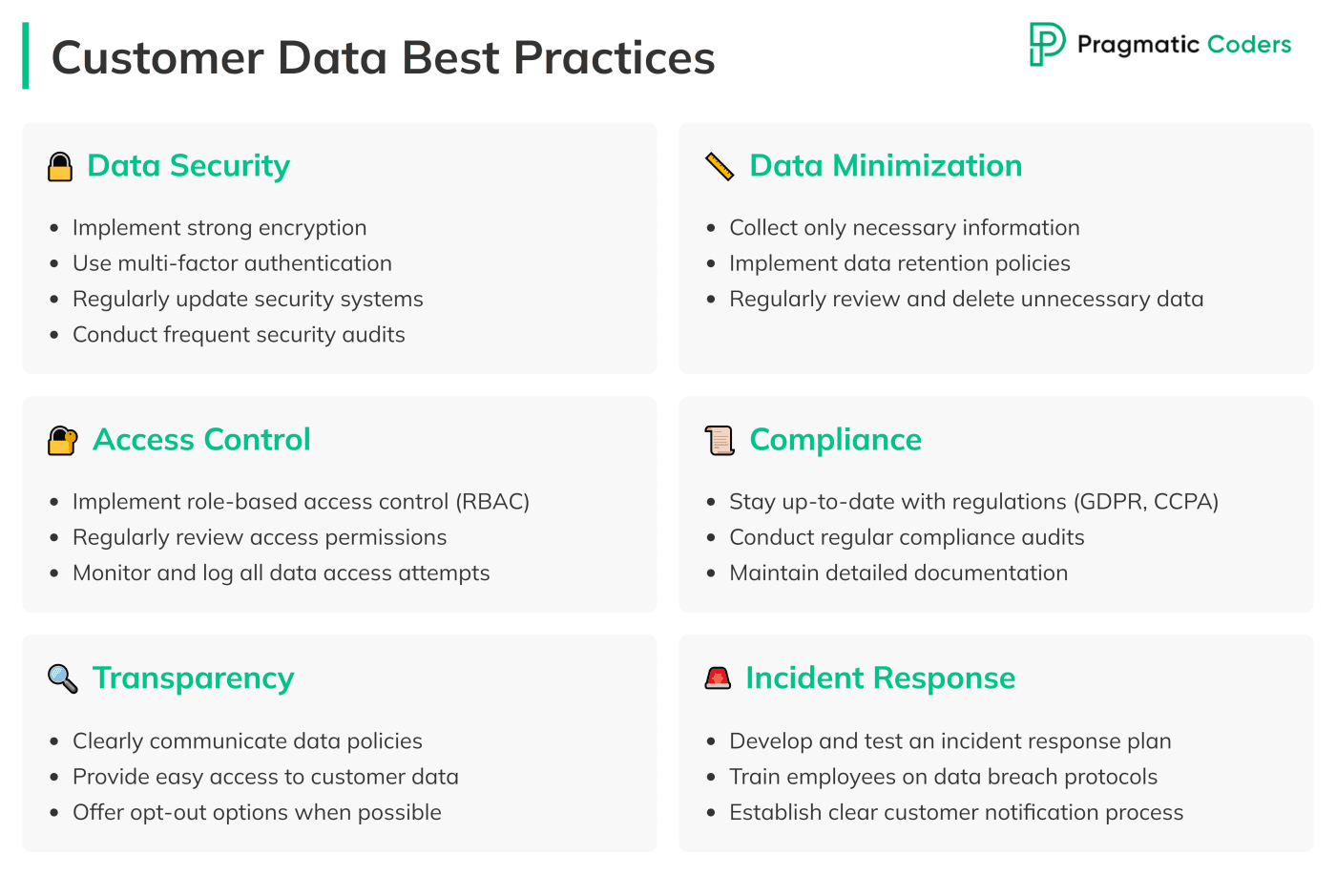
Best Practices for Handling Customer Data
Handling customer data carefully is central to staying compliant. Here’s how to ensure you’re doing it right:
- Data Minimization: Only collect the data you need. The less data you handle, the lower the risk if a breach happens, and the easier it is to stay compliant with regulations like GDPR.
- Encrypt Data: Always encrypt customer data, whether it’s being transmitted or stored. This ensures that even if the data is intercepted or stolen, it can’t be accessed without the decryption key.
- Control Access: Make sure that only the right people have access to customer data. Use role-based access controls so that employees can only access the data necessary for their role. Regularly review who has access and update these controls as needed.
Case Studies
Examples from the fintech industry can highlight how effective API security practices can protect sensitive data and build customer trust. Here are some companies that have successfully implemented strong API security measures.
Real-World Examples of Robust API Security
1. Plaid
Plaid is a major player in the fintech space, connecting users’ bank accounts to apps. They prioritize API security by using OAuth 2.0, ensuring that only authorized apps access user data. Plaid also encrypts data end-to-end, which means it’s protected whether it’s in transit or at rest. This strong focus on security has helped Plaid earn the trust of millions of users.
2. Stripe
Stripe processes billions of dollars in online payments, so their API security needs to be top-notch. They use tokenization to replace sensitive payment information with tokens, which makes it useless to hackers. Stripe also conducts regular security audits and penetration tests to catch vulnerabilities before they can be exploited. Their commitment to security has made them a trusted partner for businesses worldwide.
3. Revolut
Revolut, a fast-growing digital bank, makes security a priority by using advanced encryption and multi-factor authentication (MFA). Just like Plaid, Revolut uses OAuth 2.0. They also monitor traffic in real-time, allowing them to detect and respond to threats quickly. These security measures have enabled Revolut to scale rapidly while keeping user data safe.
Lessons Learned and Key Takeaways
Here’s what we can learn from these fintech leaders:
- Strong Authentication Matters: Plaid and Revolut use OAuth 2.0 and MFA to ensure that only authorized users can access APIs. This is critical for preventing unauthorized access.
- Encrypt Everything: Both Plaid and Stripe encrypt data in transit and at rest. Encryption is essential for keeping sensitive information secure from hackers.
- Regular Testing is Crucial: Stripe’s use of regular security audits and penetration testing shows the importance of finding and fixing vulnerabilities before they’re exploited.
- Stay Vigilant with Real-Time Monitoring: Revolut’s real-time monitoring is a great example of how staying alert can help you respond to threats as they happen.
Conclusion
API security is crucial for Open Banking. It’s what allows fintechs to innovate without compromising customer data. Strong security measures protect sensitive information, build customer trust, and keep you on the right side of regulations. Without it, the risks are too great—breaches can cost millions and seriously harm your reputation.
For fintechs, the takeaway is simple: make API security a top priority. Use strong authentication, encrypt your data, and regularly test your systems for weak spots. Stay alert with real-time monitoring, and ensure your security practices meet regulatory standards. By following these steps, you’ll protect your business, earn customer trust, and set yourself up for success in the fast-moving world of Open Banking.







